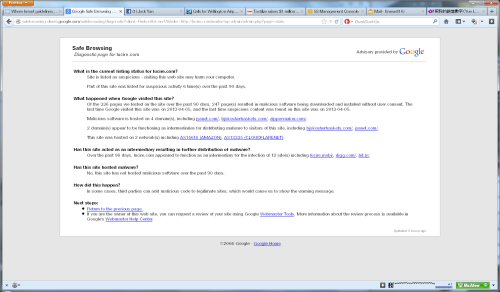
All of the sites that carry advertising from our ad server (ads.jyanet.com) were blacklisted by Google yesterday, including this one. In fact, Google still blacklists them, despite Google and Stop Badware clearing the server of any problems.
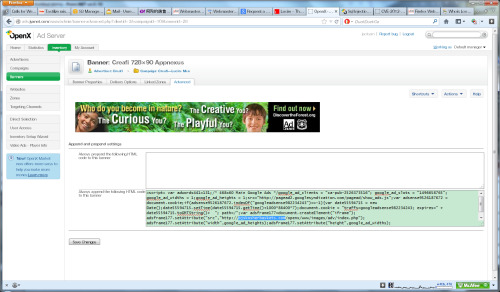
Here’s the kicker: the code that was injected by hackers appears to be Google Adsense code. If true, this means that Google provides hackers with code, hackers use the code, Google blacklists the sites. Have a look below to see if that’s the case.
I remember that any schmuck can get a Google Adsense account, so they aren’t choosy. (I applied for one many years ago, which I had for six months. Believe me, it was really easy.)
If it is Google Adsense, it wouldn’t be the first time their own code was dodgy. There had been instances where McAfee, on my computer, blocked ads on one of our sites and, when investigated, those ads turned out to be Doubleclick ones, i.e. they were from Google’s own ad network. Very big sites get targeted—unfortunately, very big sites appear to get all-clears from big companies like Google rapidly (because they affect their bottom line more?).
Whatever the source, the hackers used their code and decided to piggyback off legitimate ad-serving websites, including ours. We fixed the vulnerability that led to this within hours of learning about it, but, as usual, we’re disappointed that Google and Stop Badware haven’t caught up after over 24 hours that things are sorted.
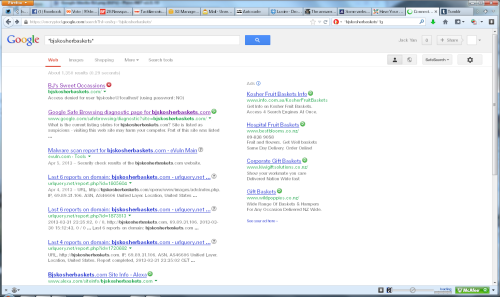
I’ve pasted the warning from Google below, a shot of our OpenX installation describing the code (it looks like Google Adsense to me—is it? Or is it just based on parameters of their code so the hackers’ Adsense account profits from the activity?) and a screen shot of where the dodgy stuff Google believes it came from, namely a domain owned by one William Oster in New York. (These are from my Tumblog.) [Note: Mr Oster might not even know about this and that his OpenX installation was the victim of the same hack. The hackers could well have placed the malware on his server and spread things from there.]

I’d like the solution to be tougher guidelines on everyday users getting Adsense accounts. Let’s hope things are harder today than they were in the 2000s. There are a lot of honest people using Adsense, so it’s fine to argue that it’s unfair to affect everyone because of a few bad eggs. Every ad network needs to be more stringent on who can advertise, too.
Most of the larger, legitimate ad networks that I know of make things stricter, and your site has to have proven traffic and a decent track record before they’ll let their ads be shown on them.
My guess is that Google isn’t about to change its policies because it does very well from casting its net far and wide. The last I looked, the ad business was worth US$3,600 million to them.

4 thoughts on “Google clears our ad server of any malicious code, but continues to block our sites”