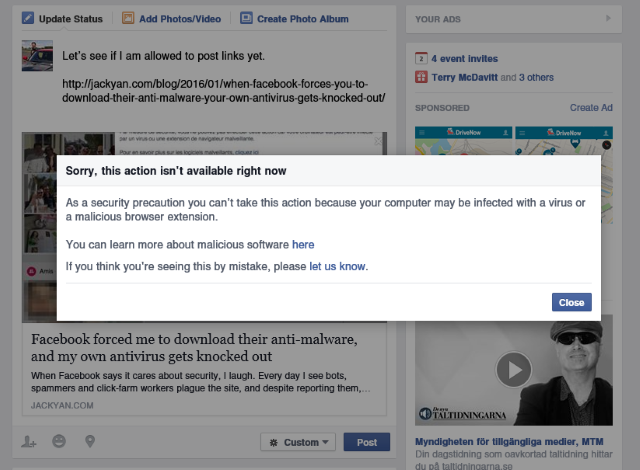
An interesting weekend on Facebook. Despite regaining access, I’m not allowed to post links (with the accusation that my computer is infected—see above), and after considerable research, I know this to be completely untrue. The Facebook malware accusations are targeted at certain users and, from the tiny sample of four that have responded to me, we are all heavy users. Just as I theorized back in June 2014 when Facebook shut down for me for 69 hours, some of us have reached a limit on their servers.
Boffins, and Facebook, say that that’s impossible, but there have been countless signs of that over the years. Most were recorded on Get Satisfaction before Facebook shut down that community (how convenient). Among them were things such as Facebook being unable to show me every video I had uploaded—the list began at 2011 and earlier ones were omitted—and the many occasions where I could no longer post, comment, like or share. There’s a direct parallel to my experiences on the former Vox.com, which Six Apart confirmed in 2009 and which they had no official answer for.
What’s the best course of action if Facebook accuses you of malware and forces you to download one of their programs from Trend Micro, F-Secure or Kaspersky? Delete your cookies. Once you do that, you can regain access, though, like me, you’ll have a limited account where link-sharing is impossible. Initially, I was able to share a few links after my accessing Facebook, but it eventually became a blanket block, with the odd one getting through (two a day in my case).
If you want to be extra-safe, run the free version of Malware Bytes. The free one won’t conflict with your existing antivirus set-up (I’m not trying to do Malware Bytes out of money), but, like the rest of us, you’ll likely discover that your system is clean.
One woman got around this by downloading a new browser, although she was also limited on the link-posting.
Whatever you do, do not listen to these big firms. Facebook, Google et al are, as I’ve been documenting over the years, particularly deceptive. I’ve still had to deal with the remnants of Facebook’s scan switching off McAfee, nearly two days later.
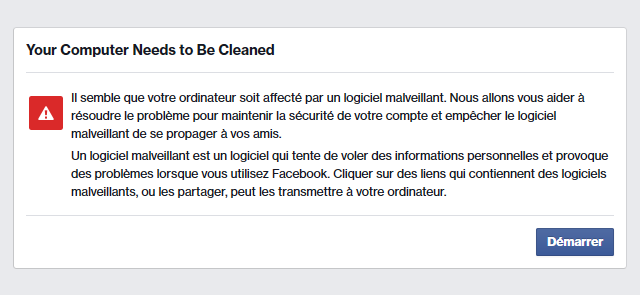
Facebook’s apparently had many complaints about this since 2014, so I’m hardly the first to encounter it. Blaming malware for their own databasing issues is cheap, but enough people will believe it—even with my mistrust of these big Silicon Valley firms I still did their malware scan, not thinking I had a choice if I wanted to access the site again. What it really did during the scan is anyone’s guess.
I’d rather they come clean and tell people: you are allowed x posts a day, x links a day, and x photos and videos a day. I can work around that. But if they came clean about this and the number of click-farm workers and bots plaguing the site, what will that do to their share price?
And isn’t it ironic I can presently share more, and have more freedom of speech, on Weibo, monitored by the Chinese Communist Party?
PS.: As of the last week of April, I have had two reports that deleting cookies does not work, but switching browsers does. Facebook appears to find a way to identify you, your regular browser and your IP address together, without cookies.
P.PS.: Mid-May, and from my other thread on this topic, in the post-postscripts: ‘Andrew McPherson was hit with this more recently, with Facebook blocking the cookie-deleting method in some cases, and advises, “If you get this, you will need to change your Facebook password to something very long (a phrase will do), delete and clear your browsers cache and history, then delete your browser, then renew your IP address to a different number and then reinstall your browsers.” If you cannot change your IP address but are using a router, then he suggests refreshing the address on that. Basically, Facebook is making it harder and harder for us to work around their bug. Once again, if you sign on using a different account using the same “infected” computer, there are no problems—which means the finger of blame should remain squarely pointed at Facebook.’
P.P.PS.: June 17: as detailed at my other post, for those who might find Andrew’s method too technical, the current wisdom is to wait it out. It does appear to take days, however. Reminds me of the time Facebook stopped working for me for 69 hours in 2014. Do not download Facebook’s crap.
@hobbinator @jackyan @AnnaVsLife @facebook mine is back to normal now. It seems to have just needed time to fix itself.
— MrsMcCharms (@MrsMcCharms) June 16, 2016
@MrsMcCharms @jackyan @AnnaVsLife @facebook Mine finally reset too, phew! Did NOT download/run … no malware, no need! Such BS!
— Kimberly Jennery (@hobbinator) June 16, 2016
P.P.P.PS.: November 30: it appears waiting it out is the best option for those who don’t want to mess around under the bonnet. Shawn Picker, in the comments, says to expect a five-day wait.
P.P.P.P.PS.: May 9, 2017: On the other post on this subject on my blog, a user called David suggested modifying your headers and to fool Facebook into thinking you are using another type of device. In comment no. 66 below, Stephan confirms that it works and gives more details about it. Check it out!
P.P.P.P.P.PS.: October 24: Again in the other thread on this topic, Don Dalton found that he was able to replace his Chrome profile with an older one to bypass Facebook’s block. Have a read of his comment here.
P.P.P.P.P.P.PS.: February 18, 2018: over the last few weeks, Mac users have been getting hit hard with this fake warning, and are being offered Windows software to download (which, of course will not work). Some have reported that changing browsers gets them around this. Downloading the equivalent anti-malware program from the same provider (e.g. Eset) does nothing, since the one user I know of who has done this came up with a clean Mac—because, as we already know, the warnings are fake.
P.P.P.P.P.P.P.PS.: February 23, 2018: finally, a journalist has taken this seriously! Louise Matsakis, a writer for Wired covering the security and social media beats, has looked into the latest round of Facebook malware warnings being forced on Mac users. Facebook is still lying, in my opinion, claiming there could really have been malware (lie number one), but the company’s probably so used to saying one thing and doing another by now. Louise is right to seize upon the fact that no one knows what data are sent to Facebook during the scan. It’s a fine article, and I highly recommend it.





I’m not entirely sure if it’s available for Linux, but on Firefox for Windows it was called Change Headers, and for Chrome for Windows it’s called Modify Headers for Google Chrome. The last two postscripts have links to the comments where some users explained how they worked. Best of all, it isn’t made by Facebook!
I just had the same thing happen. I simply setup a VM with a clean copy of Win10 and let it scan that. Scan came back clean and I deleted the VM. Problem solved.
Good idea, csorrows. I think setting up a VM may be beyond the expertise of a lot of users, but it is a fine solution.
Try to login from Linux based device, their sh*t will not run on it and therefore they remove their “suspicion” from your account. Worked for me.
To follow up on this, maybe changing browser’s agent to fool FB to think you are logging in from Linux device.
Funnily enough I encountered exactly the same problem today when I tried to log into Facebook. First time I had ever seen it. Tried the obvious of different browser, clean cache, history, different machine, etc. That made no difference. Then I tried the same method employed by csorrows – normality was restored.
If this becomes a common feature of Facebook “security” – then Facebook will find itself permanently running in a very lonely browser in a very boring virtual machine.
It has happened to me twice. Once in 2016 immediately after I shared a Google photos video which was mine. I was blocked for three days and never received any reply to the countless complaints I sent. The next was last month (Nov 2017) immediately after I shared my Ebates referral link. I logged in through Firefox on the same computer and it allowed me to login in with limited access. I cleared my cookies on Chrome and the same thing happened, suddenly five minutes later it was like nothing happened. Either way, both times happened the moment I shared a link. I’m a systems engineer and it was a fresh OS install that was hardened.
Thank you, Dusty, it’s useful to get the viewpoint of a professional. I’ve had trouble sharing links on Facebook for years, long before this malware scanner, so my mind keeps coming back to some databasing fault on their end. Do you think this theory is plausible?
Well said, Normski. I ceased updating my Facebook wall in 2017. It really has less and less utility for me, and these fake malware accusations don’t help its cause.
I am having this problem today. I have a MacBook Pro and FB’s software won’t run on it. Its’ only for Windows. What a bunch of crap. I use FB for my business an now I am locked out except on my phone. I guess I will wait it out and see what happens. I tired Safari and Chrome and neither will work.
Roxane, till Facebook gets its act together, can you try accessing m.facebook.com (the mobile version) on your Macbook? It’s not a proper solution but might prove to be a workaround.
I’ve just downloaded their anti-malware ESET_T10157058615938835T_.exe and let it run. Immediately closed browser, opened Task manager and ended process Eset Facebook… Restarted comp. and all ok.
Thank you for sharing your experience, Fantast. How many hours did it take to run? A lot of us ran it and it never completed over many hours. Also, were you able to get rid of it from the hidden directory on your computer? We still can’t ignore the fact your computer was probably never infected to begin with.
And what if you have a Mac?
In 2016, Macs weren’t affected, as I was able to get on by going to a Mac OS X machine. I’d still recommend the same course of action: to change the headers and find a device they haven’t blocked (e.g. an Iphone). The other option is to wait three days—for most people it comes back.